In this session of CCNA tutorials, we are going to discuss the wireless principles in computer networking. This section covers the CCNA 200-301 exam topics : wireless principles, non-over lapping channels, SSID, Radio frequency, and Encryption. Let us understand each topic one by one.
Wireless Principles in Computer Networking
Introduction to Wireless Principle
The wireless principle refers to the concept of wireless communication where communication takes place between two entities without connecting the physical wires or cables. In wireless communication, the signal or data travels in free space in the form of electromagnetic waves. The transmitting and the receiving stations use the same radio frequency channel to communicate with each other. The transmitter sends the data in the form of alternating current. When the alternating current reaches the antenna, it then propagates through antenna in the form of electromagnetic waves. The receiving station receives the signal through the antenna and converts them back to the original data.
The major issues with the wireless communication are data security and the collision. Since, wireless signal propagates through free space, any unknown station that is within the range of WI-Fi signal can intercept the wireless data. Hence,various types of data encryption techniques are used to protect the data privacy.
Another concerning factor is when many stations transmitting the signal at the same time, it can cause collision of frames transmiiting from multiple devices . CSMA /CA (Carrier Sense Multiple Access /Collision Detection) technique is used to avoid collision of frames. In wireless network, the entire devices wait for their turn to transmit, until the other devices stop or complete its transmission, then it retransmits the data.
Non overlapping of Wi-Fi channels in Wireless Principles
The wireless local area network is defined in 802.11 by IEEE. The wireless LAN is commonly named as Wi-Fi. However, the term “Wi-Fi” is the trademark of Wi-Fi Alliance. The task of Wi-Fi Alliance is to test and certify the wireless devices for IEEE 802.11 standards. It also checks for interoperability and compatibility of wireless equipment manufactured by different vendors.
Wi-Fi uses two bands of radio frequency namely 2.4 GHz and 5 GHz. These two bands of frequencies are called ISM band. ISM stands for Industrial Scientific and Medicine. These two bands of frequency spectrums are free to use. We don’t need to have licence or permission from frequency governing authirity such as SACFA (Standing Advisory Committee on Frequency Allocation) to use the channel within ISM band. All the home appliances, access points, cordless phones use the frequency range of ISM band within their limited range.
Each of 2.4 GHz and 5 GHz are further divided into multiple channels.
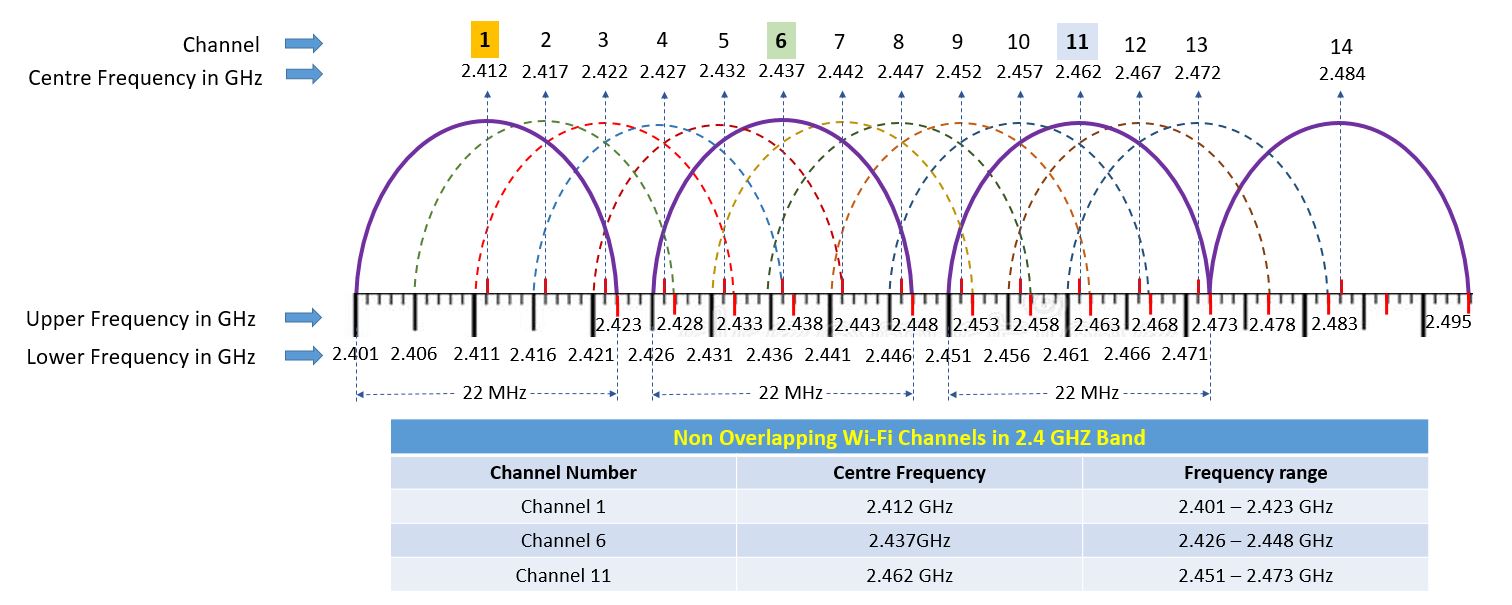
2.4 GHz band uses the frequency spectrum for 2041 to 2484 MHz or 2.401 to 2.484 GHz. It is divided into 14 channels having 5 MHz channel spacing. Each channel is 22 MHz wide. However, each channel is separated by 5 MHz to its adjacent channel and the width of the entire band of 2.4 GHz is 100 MHz. As a result, 11 channels are overlapped within 100 MHz wide. Only channel 1, 6 and 11 are not overlapped with each other on entire 2.4 GHz band. The channel 1, 6 and 11 are called non overlapping channels.
In smaller wireless network, single access point is generally used. Hence, you can use any channel for wireless communication. However, for large network where multiple access points are to be installed, access points transmitting at the same frequency interfere with each other.
Hence, using non overlapping channels, there will not be any co-channel interference with adjacent Wi-Fi network.
| Channel Number | Centre Frequncy in MHz | Frequency Range in MHz |
| 1 | 2412 | 2401-2423 |
| 2 | 2417 | 2406-2428 |
| 3 | 2422 | 2411-2433 |
| 4 | 2427 | 2416-2438 |
| 5 | 2432 | 2421-2443 |
| 6 | 2437 | 2426-2448 |
| 7 | 2442 | 2431-2453 |
| 8 | 2447 | 2436-2458 |
| 9 | 2452 | 2441-2463 |
| 10 | 2457 | 2446-2468 |
| 11 | 2462 | 2451-2473 |
| 12 | 2467 | 2456-2478 |
| 13 | 2472 | 2461-2483 |
| 14 | 2482 | 2473-2483 |
SSID (Service Set Identifier)
The SSID stands for Service Set Identifier. It is a unique identifier consisting of 32 alphanumeric characters used to identify the Wi-Fi network.
An SSID can be thought of as the name of a wireless network. It is a unique identifier that distinguishes one wireless network from another. Just like how each house on a street has its own address, every wireless network has its own SSID. When you search for available WiFi networks on a device, you’ll see a list of SSIDs that are within its wireless range.
Why is SSID important?
The SSID is important because it enables devices to connect to the correct wireless network. When you want to connect to a specific WiFi network, you need to know the SSID so that your device can locate the network.
In addition to helping devices find and connect to the correct network, the SSID also plays a role in securing the network. Most modern routers and access points allow you to configure the SSID to specific security protocols, such as WPA2 or WEP. By setting a secure SSID, you can prevent unauthorized access to your network and ensure that only authorized users can connect.
In addition to helping devices find and connect to the correct network, the SSID also plays a role in securing the network. Most modern routers and access points allow you to configure the SSID to specific security protocols, such as WPA2 or WEP. By setting a secure SSID, you can prevent unauthorized access to your network and ensure that only authorized users can connect
Radio Frequency
The radio frequency is the rate of oscillations of electro-magnetic waves that ranges from 3KHz to 300 GHz. In other words, radio frequency is the number of cycles of alternating current that propagates through the metallic antenna in the form of electromagnetic waves.
Electromagnetic waves are the waves that are generated as a result of vibration between electric field and magnetic field. While transmitting the data, it is in the form of alternating current. When it reaches the radiating antenna, it creates an electromagnetic field. As a result, the electromagnetic waves radiated through the antenna.
The unit of measurement of radio frequency is Hertz. The Hertz is defined as the number of cycles per second.
Radio frequency spectrum ranges from 30KHz to 300GHz and it is divided into several bands.
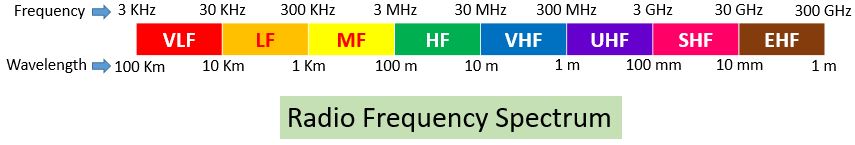
- VLF – Very Low Frequency
- LF – Low Frequency
- MF – Medium Frequency
- HF – High Frequency
- VHF – Very High Frequency
- UHF – Ultra High Frequency
- SHF – Super High Frequency
- EHF – Extremely High Frequency
| Frequency band | Abbreviation | Range of Frequency | Wavelength | Application |
| Very Low Frequency | VLF | 3 KHz-30 KHz | 100 km-10 km | Maritime Radio Navigation |
| Low Frequency | LF | 30 KHz-300 KHz | 10 km-1 km | Maritime Radio Navigation |
| Medium Frequency | MF | 300 KHz-3 MHz | 1 km-100 m | Aviation radio Navigation, AM radio Broadcasting |
| High Frequency | HF | 3 MHz-30 MHz | 100 m-10 m | short wave radio broadcasting |
| Very High Frequency | VHF | 30 MHz-300MHz | 10 m-1 m | FM radio, VHF television, mobile radio communication |
| Ultra High Frequency | UHF | 300 MHz-3 GHz | 1 m-100 mm | Mobile phones, GPS, Wireless LAN |
| Super High Frequency | SHF | 3 GHz-30 GHz | 100 maximum | Radio Astronomy, Wireless LAN, Modern Radars, Satellite Television broadcasting |
| Extremely High Frequency | EHF | 30 GHz-300 GHz | 10 mm – 1 mm | Radio Astronomy, satellite communication |
The frequency is inversely proportional to the wavelength. The wavelength is the measure of distance between the crest and troughs of two successive cycles. It is measured in meters. As the frequency increases, the wavelength decreases. Hence when we move from lower to higher frequency, the wavelength of the radiating waves starts deceasing.
The radio frequency is used in any applications such as cordless phones, cell phones, radio transceiver, broadcasting station, satellite communication, Wi-Fi, Bluetooth and other home applications like microwave ovens, tv remote etc.
Wireless Encryption
Security is a major concern in wireless communication. The wireless devices like access points, wireless routers need to be secured using some encryption technology. Since, the wireless devices that are transmitting the wireless signals may be intercepted by the unknown stations. Hence there must be some mechanism to restrict the unknown stations intercepting the signal.
There is certain wireless security protocols that are being implemented in wireless security.
Encryption is the method of converting plane data into cryptic form. The encrypted data is transmitted using cypher code and the data is converted back to its original plan format by decrypting it at the receiver end.
Wireless encryption is used to secure the wireless data when it is transmitted through free space.
In wireless communication, encryption plays a major role in securing wireless data.
Authentication protocols are used to secure wireless network. A password or an authentication key is needed to connect to the wireless device.
Some of the important wireless encryption protocols are.
- WEP – Wired Equivalent Privacy
- WPA – Wi-Fi Protected Access
- WPA2 -Wi-Fi Protected Access 2
- WPA2 -Wi-Fi Protected Access 3
WEP (Wired Equivalent Privacy)
It is one of the earliest wireless encryption protocols and was developed in 1999. WEP makes the use of RC4 encryption algorithm to secure the wireless data. WEP was not predominantly strong to secure wireless device. It uses only 64-bit encryption, that is why it was easier for the hackers to crack the password of the wireless device with least secure password. WEP is no more used or rarely used in some old wireless devices.
WPA (Wi-Fi Protected Access)
WPA replaces the least secure WEP standards and officially launched at 2003. WPA uses PSK and TKIP for encryption. PSK stands for Pre-Shared Key, whereas TKIP stands for Temporal Key Integrity Protocol. It uses 256-bit encryption mechanism that leads to considerable enhancement in securing wireless devices. WEP is backward compatible with WEP. However, the cyber experts have found many vulnerabilities.
WPA2 (Wi-Fi Protected Access 2)
The major flaws in WPA leads to the development of WPA2. WPA2 was officially launched in 2006. Its use AES and CCMP by replacing TKIP and PSK. CCMP stands for Cipher Block Chain Message Authentication Protocol, whereas AES stands for Advanced Encryption Standards. However, KRACK (key reinstallation attack) vulnerabilities exposes the weakness of WPA2.
WPA3 (Wi-Fi Protected Access 3)
WPA 2 uses 4-way authentication. In 2017 security expert found a major flaw in WPA2. KRACK attack vulnerability.
WPA 3 is the latest wireless encryption protocol. It was developed in 2017. It provides cutting edge wireless security protocols to the market. It has simplified the process of Wi-Fi security and provides the most robust authentication for the wireless devices. It has both personal and enterprise security feature.
WPA 3 uses GCMP for encryption. It has some additional features like PMF (Protected Management Frames) that prevents 802.11 management form eavesdropping and forging. One more feature is SAE (Simultaneous Authentication of Equals) that protects 4 ways handshaking when used in personal mode. The forward secrecy is another unique feature in WPA3 that helps to prevent the encrypted data being transmitted on the air. so that the attackers can decrypt it in the middle.
| ←Prev | Next→ | |
| Verify and Configure IPv6 Address | Virtualization in Computer Networking |





