In this section, we will be going to explain the different types of password cracking techniques used by hackers to gain access to your accounts and your systems anonymously.
Password Cracking
Password cracking is a process or a technique to identify or gain access to the forgotten password of any user’s account. Password cracking is achieved by using a number of techniques such as by repeatedly guessing, by using algorithm technique, by matching common keywords, etc.
Password cracking may be done for a legitimate reason or recover a forgotten password, but most of the time, this activity is being illegally performed by the hackers to gain access to the other’s account.
Let us discuss some of the prominent password cracking techniques:
- By guessing
- Brute force attack
- Rainbow table attack
- Dictionary attack
By Guessing
This is the most common and the easiest method of cracking someone’s password. The cracker may use third-party software dedicated to this task and passwords are generated randomly. These randomly generated passwords are based on keywords related to the victim’s personal information like hobbies, favorite dish, favorite game, family details, most loved ones name or surname, his/her area of interest, etc.
Brute force attack
This type of attack uses non-dictionary terms to create a possible password by the combination of alphanumeric characters and special characters. The attacker tries different combinations of possible passwords by permutation and combination method. But, it needs repetitive actions to gain access to the password. It is possible when password length is of few characters. But, it is a very lengthy process and time-consuming to crack the long passwords by using this technique. It even takes years to crack a moderate password.
Rainbow table attack
The Rainbow table is a hash function for storing the hashed passwords. Generally, the password we entered in the computer system is not stored as a plain text for security reasons. Hash encryption is used to alter the characters of the password. It is a one-way function and hence cannot be decrypted back.
The password entered by the user is converted into the hash value. It is then compared with the stored hash value. If the converted hash value is matched with the already stored hash value, then the authentication is granted to the user to access the account.
Dictionary attack
This type of attack uses a very large set of keywords based victims’ valuable information such as his date of birth, spouse name, marriage anniversary, children’s name, place of birth, pet name, etc. to crack the potential password. Most often, the victim has the habit of keeping the password as simple as possible, because they are easily memorable. But, the attacker searches for such vulnerabilities and tries all possible keywords related to the victim’s information.
How hackers try to crack the password
It is not an easy task to crack someone’s password so easily. Generally, passwords are not saved in plain text in the database of the webserver. When we type the password on the login screen, it is hidden with the series of black dots. But, it is just visually hidden from your eyes. The information you type on the login screen is your USER ID and Password. Most of the time user id can be your email address or mobile number or some other characters that are visible to you while typing. The information you enter to the screen is actually saved in the back end database of the company’s server. The user name is saved as a plain text, but the password will not be saved in plain text even in the backend database.
The Hash algorithm is used to store the password in the database of the server. Hashing algorithm helps to encrypt and manage the password. Hence the password is stored in a database in the encrypted format. There are many types of the hashing algorithm used by database managers such as MD5, MD6, SHA-1, SHA-2, and many more.
Let us take an example of Facebook Account how passwords are managed and how hackers try to gain access using the password cracking technique mentioned above. Suppose you want to open a new account on Facebook, you will go to the Sign Up page and starts typing your personal information to the signup page. The information you entered can be your name, date of birth, country, gender, email id, contact number, and so on. You also create a unique user id and password to log in to the Facebook site.
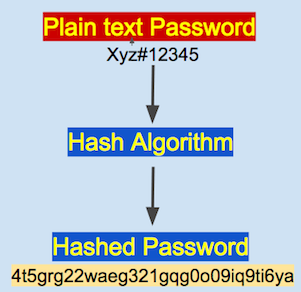
Now, all the information you entered will be saved in the database of the backend server as it is, except the password. That means all your information is saved as plain text. But, what about the password? Passwords are never saved in plain text. There comes the role of the Hashing algorithm.
The password you entered is combined with a Hashing algorithm to get encrypted output. Remember, a Hashing algorithm is a way one function. The encrypted password cannot be reversed back. Nowadays, almost all the company’s’ servers use hashing techniques to encrypt the password. So, it is not that easy to crack a password.
Now, a hacker wants to breach your Facebook account information. He can gain access to all the information, except password because the password is not saved as a plain text. Even, the decrypting process cannot be performed because the hash is a one-way function.
But, hackers try numerous ways to crack the password. Now, the strength of the password comes into play. The strength of the password means how complex the combination of characters is contained in the password, The more complex combination of the characters, the harder or almost impossible to crack the password.
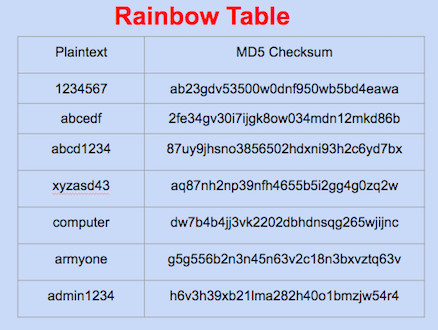
To crack the hashed passwords, hackers take the help of the Rainbow table, the Rainbow table contains the password hashes of commonly used passwords along with their plain text format. If the hashed value matches with the rainbow table, your password has been cracked. But, it seems to be easy in theory only, practically it is very hard to gain access, especially the complex passwords are almost impossible to crack.
To prevent the rainbow table attack, the company uses a salt technique to make it even more encrypted.
Salt Algorithm
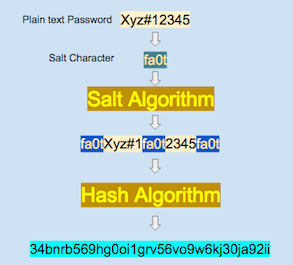
In salting, a specific combination of characters is inserted in the specific position of the plain text password before hashing. Every company has its own hashing algorithm and this algorithm is kept very secret. Let us understand, how salting is done to the plain password.
Let us say, the Facebook algorithm inserts salting characters fa0t in between the plain passwords, the final passwords look as shown in the figure above, and then the hashing is done.
When salting is used rainbow table attack is of no use, even if a low strength password is used. Almost all the webserver who serves financial transaction like banking, payment gateway use salting techniques to prevent such attack.
Now, hackers try another method to gain access to your account. This is called a dictionary attack. The dictionary attack is based on the valid dictionary keyword. All possible keywords are contained in the worllist.txt file. The hacker writes a code to match the hashed password with the wordlist.txt file. The dictionary attack is possible when you create a password having your favorite keywords.
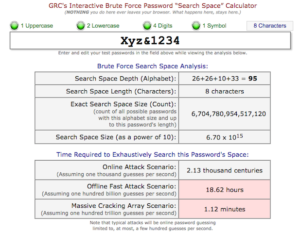
Another method to crack the password is a brute force technique. Hackers use brute force analysis software to get the exact combination of passwords. All possible combinations of keyboard characters, numbers, and special symbols are tried using permutation and combination methods. But, this technique may take lots of time even a couple of years to extract the matched password.
So, these are the major techniques hackers try to gain access to your account information.
How to protect yourself from password breach
The following tips may help you to keep and manage your password safe.
- Always use strong passwords to keep yourself safe from hacking.
- Practice good length of password more than 8 or 10 characters.
- Use the combination of numbers, alphabets, and special symbols.
- Your password should contain at least one upper case, lower case, numbers, or symbols.
- Don’t ever use common keywords such as your pet name, your child’s name, spouse name, date of birth, your wedding anniversary year and so on
- Use different passwords for your different email accounts, net banking accounts, or other web services accounts. If anyone of them breached, rest imagine yourself.
- Don’t ever write your password in a diary or paper. It’s better to memorize your password by hard.
- Change your password periodically.
- Don’t share your password with anyone.
- Always opt for two-factor authentication to keep yourself safe from security.
- The best practice is to use a virtual keyboard while logging in to your email and net-banking account.
If you like the article, please share through:


hello sir